What Is a SOCKS Proxy? The Simple Guide That Clears It Up

SOCKS proxy is often associated with online privacy, bypassing restrictions, managing multiple connections, etc. If you’re someone trying to use SOCKS proxy for the same, maybe you’ve wanted to know more about it or are trying to set it up on your device. Don't worry—you’re at the right place.
We have developed this guide to help you get started with SOCKS proxies. You get to know what it is and its types. Plus, we have explained its architecture, configuration, use cases, and challenges, so you’re all covered.
What is SOCKS Proxy?
To begin with, SOCKS stands for Socket Secure. It is a network protocol that helps route traffic between a client and a server through an intermediary. Introduced in the early 1990s by David Koblas, it has evolved since then with a focus on better security, speed, and control.
Getting into the details, the SOCKS proxy works in the session layer of the OSI model. This position makes it compatible with protocols like HTTP, HTTPS, FTP, POP3, and SMTP. Plus, the applications that rely on both TCP and UDP.
The reason SOCKS proxy is preferred over others is that it can overcome the crucial limitation that comes with regular web proxies. It isn’t restricted to browser traffic and works with different kinds of traffic.
How Does a SOCKS Proxy Work?
Instead of connecting directly to the web, the device first connects to the proxy server. The SOCKS proxy acts as a middleman and manages communication on both ends (device and the internet. Why is it necessary? It hides the IP address, avoids firewalls, and gets around network restrictions.
While this is a basic explanation, it is better understood with a basic client-server model of the SOCKS proxy.
Client-Server Model in SOCKS Proxy
For a better understanding, we have broken it down by presenting it in a simplified flow.
- Client initiates connection and performs authentication handshake: The client connects to the SOCKS proxy and sends a list of supported authentication methods. The proxy selects one and, if required, the client completes authentication (e.g., username and password).
- Client sends destination request to the proxy: Once authenticated, the client requests a connection to a specific target server. The request includes the destination address (IPv4, IPv6, or domain name) and port.
- Proxy attempts to connect to the target server: The proxy uses the provided destination details to initiate a connection to the target on the client’s behalf.
- Proxy sends a response back to the client: If the connection is successful, the proxy returns a success reply. If it fails, the client receives an error and the session is closed.
- A Tunnel is established: With the connection approved, a direct tunnel is created between the client and the target server via the proxy. The SOCKS proxy forwards bytes in both directions, allowing full communication through the tunnel without modification.
Types of SOCKS Proxies
Aren't all SOCKS proxies built the same? Confused? As said before, SOCKS proxies have been evolving, resulting in different types. Understanding their types is crucial whether you want to learn or use them for your needs.
SOCKS4 Proxy
SOCKS4 proxy is the earliest version of the SOCKS protocol, and it is limited to TCP traffic. Plus, it lacks authentication, making it incompatible with backconnect proxy networks as they pass routing data through credentials. Regardless of these limitations, it's still in action, as many prefer its affordable pricing, better customization, and less complexity.
SOCKS4a Proxy
SOCKS4a is an upgrade to the SOCKS4 proxy. Instead of relying on the client to resolve hostnames, SOCKS4a allows the proxy to do it. While useful, it is rarely used in modern environments due to limited flexibility.
SSH SOCKS Proxy
Unlike SOCKS4 and SOCKS5, the SSH SOCKS proxy isn’t a conventional proxy. An SSH SOCKS proxy is created using dynamic port forwarding (like ssh -D). This way, a temporary SOCKS5 proxy can be set on your local machine. It is often used as a temporary solution to achieve secure access to remote servers.
SOCKS5 Proxy
SOCKS5 proxy addresses the limitations—it supports both TCP and UDP traffic, adds authentication, and handles different types of address formats, including IPv4, IPv6, and domain addresses. However, the only catch was that with the added capabilities, it became slightly complex.
SOCKS5h Proxy
SOCKS5h is similar to SOCKS5—the only difference is the “h” which stands for hostname resolution. This addition allows it to handle DNS lookups from the proxy end instead of the client end.
SOCKS Proxy Comparison
Want it even simpler? Here’s a quick comparison of all SOCKS proxies. We have also included HTTP proxy as many are confused between choosing SOCKS5 vs. HTTP proxy.
| Feature | SOCKS4 | SOCKS4a | SSH SOCKS | SOCKS5h | SOCKS5 | HTTP Proxy |
|---|---|---|---|---|---|---|
| Traffic Support | TCP only | TCP only | TCP & UDP | TCP & UDP | TCP & UDP | HTTP/S GET/PATCH/PUT, etc HTTP/S CONNECT (Supports all TCP traffic) |
| DNS Resolution |
Client-side |
Proxy-side | Proxy-side | Proxy-side |
Client-side |
Proxy-side |
| Authentication Support | No | No | Yes (SSH-based) | Yes (Optional) | Yes (Optional) | Varies |
| Encryption | No | No | Yes (via SSH) | No | No | Native Encryption for HTTPS |
| Supports Domain Names | No | Yes | Yes | Yes | Yes | Yes |
| Setup Complexity | Low | Low | Moderate | Low | Low | Low |
| Best For | Nothing | Nothing | Secure remote access | DNS leak prevention + UDP | UDP | Most Use Cases |
Setting Up a SOCKS Proxy Server
Implementing and configuring proxies vary based on the type of proxy. While it was slightly technical before, with proxy providers around, it has become easier. However, keep in mind that proxy providers have different offerings, and generating proxies remains unique.
With Ping Proxies, you get ethically sourced proxies (HTTP, HTTPS, and SOCKS5 TCP protocol). With an intuitive dashboard and easy-to-use configurator, you can instantly generate the proxy of your choice.
Note: The steps associated with this section vary depending on your proxy provider. For easy understanding, we’ve included steps for datacenter and residential (sticky/rotating/static) proxies.
Generate Residential Proxies with Ping Proxies
1. Sign in to Ping Proxies to get started. Once done and you’re on the dashboard, look for the “My Proxies” section in the left quick access tab and click on the ”Residential” option associated with it.
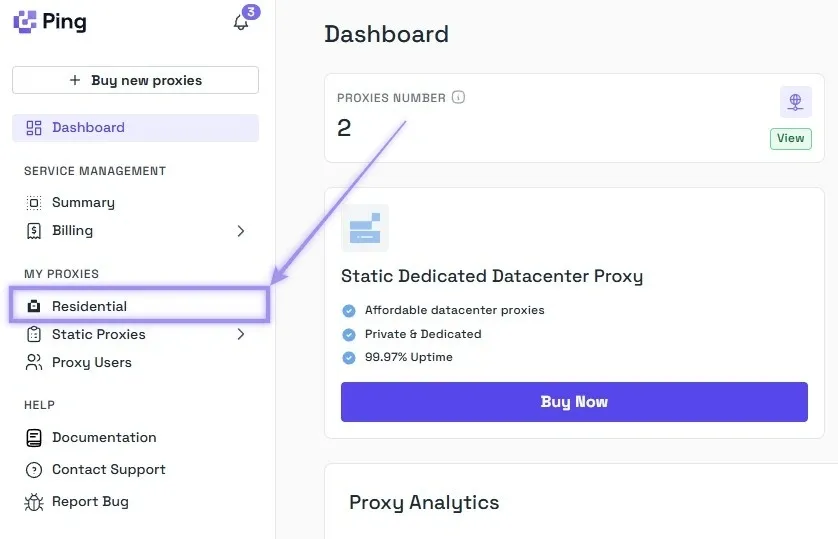
2. After the Residential Configurator is loaded, first select between rotating and sticky type. Then, select the country, city, ISP/ASN, and quantity. You can skip the city and ISP/ASN if you don’t need specific targeting, and generally, this is recommended as the less you target, the larger your available proxy pool will be. With your desired options set, click on the “Generate” button.
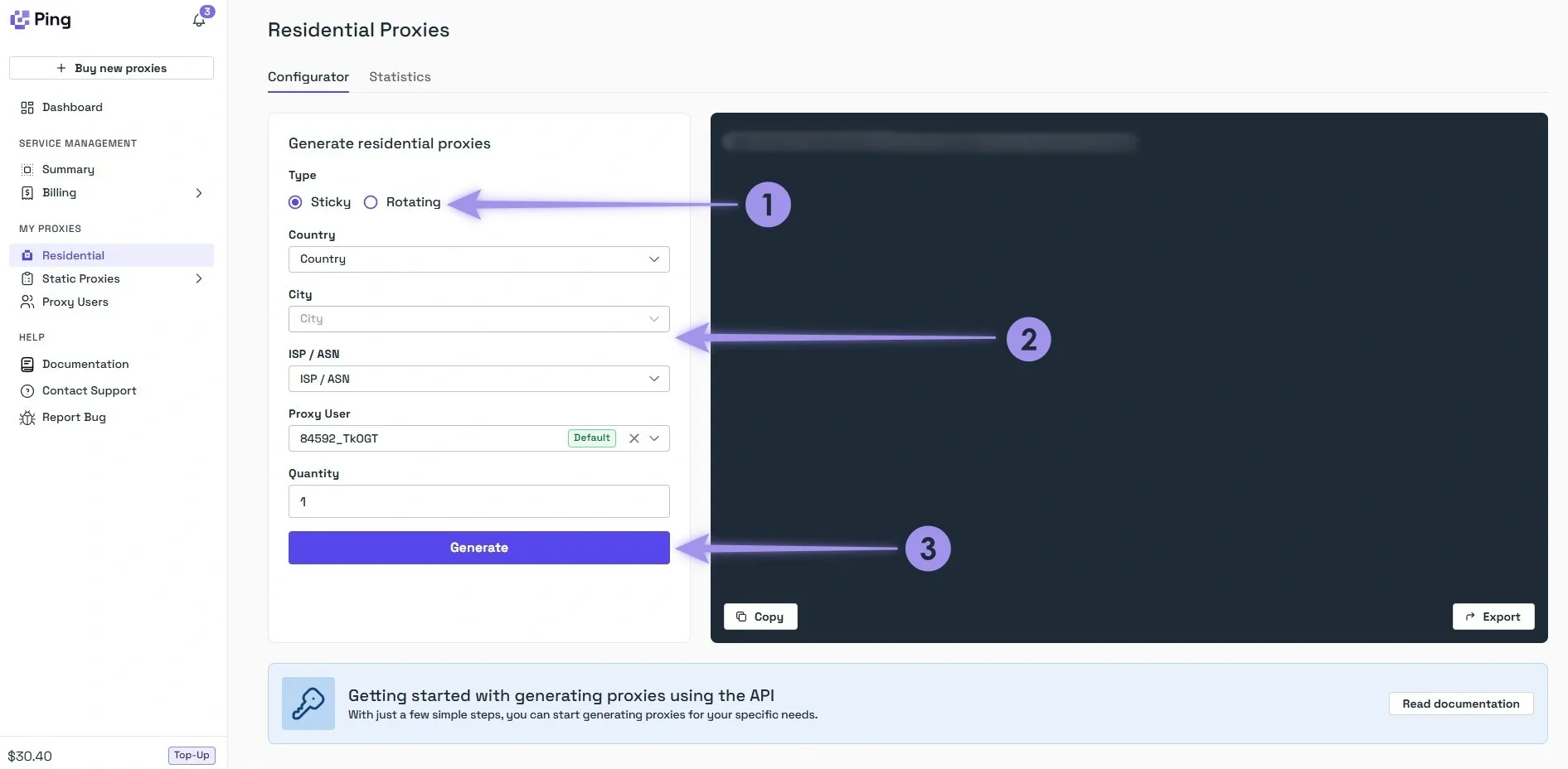
Note: For sticky proxies, don’t forget about adding the location within the username. Failing to do so routes you to the incorrect location.
Generate Static Proxies with Ping Proxies
Unlike residential proxies, static proxies don’t need generation, making them comparatively easier to work with.
1. Navigate back to the dashboard and click the “Static Proxies” option below the Residential option.
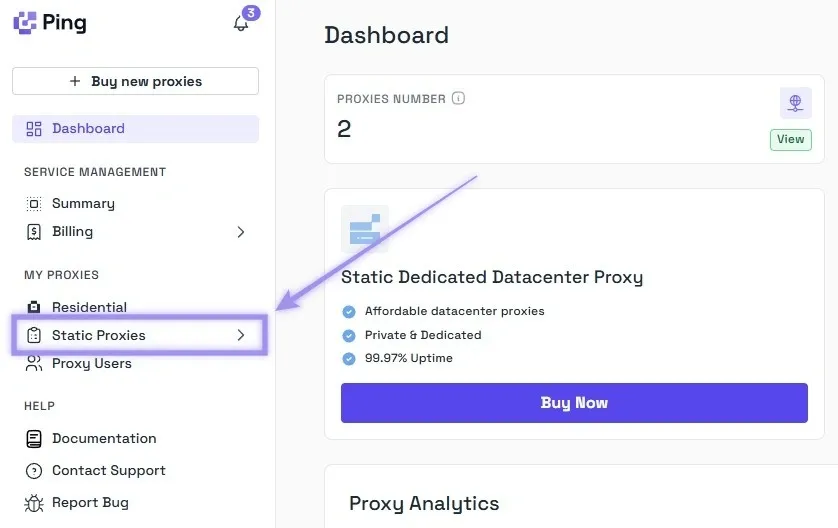
2. The list is updated upon purchasing a static proxy. You’re displayed with your username, password, IP Address (hostname), and port. All you need to do is copy and paste them into their respective fields in SessionBox One.
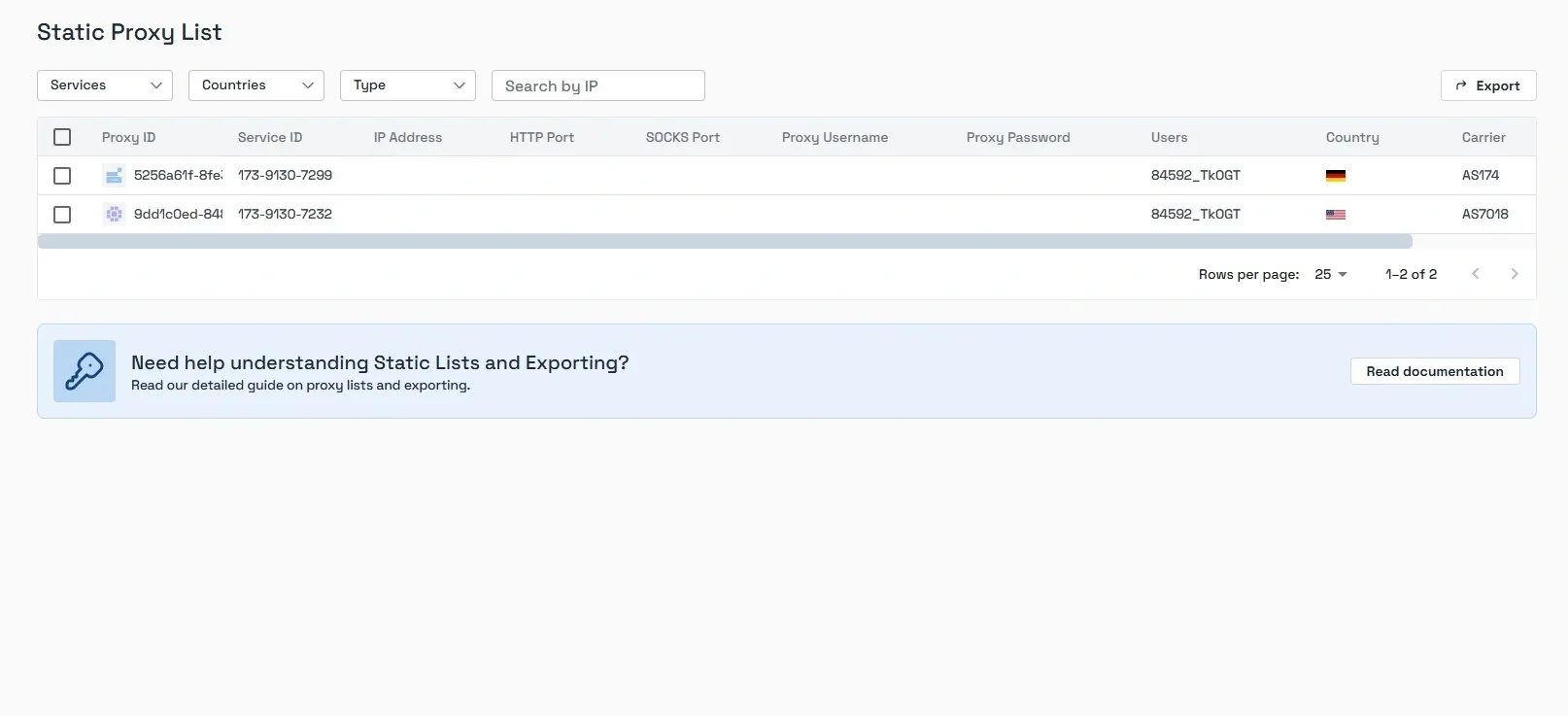
With the proxies generated successfully, you can put them to use. Here’s how to set them on different platforms.
Setup Proxy on Web Browsers
Note: The setup and proxy settings vary depending on the browser. While some rely on system settings, others have manual proxy configuration within the browser settings.
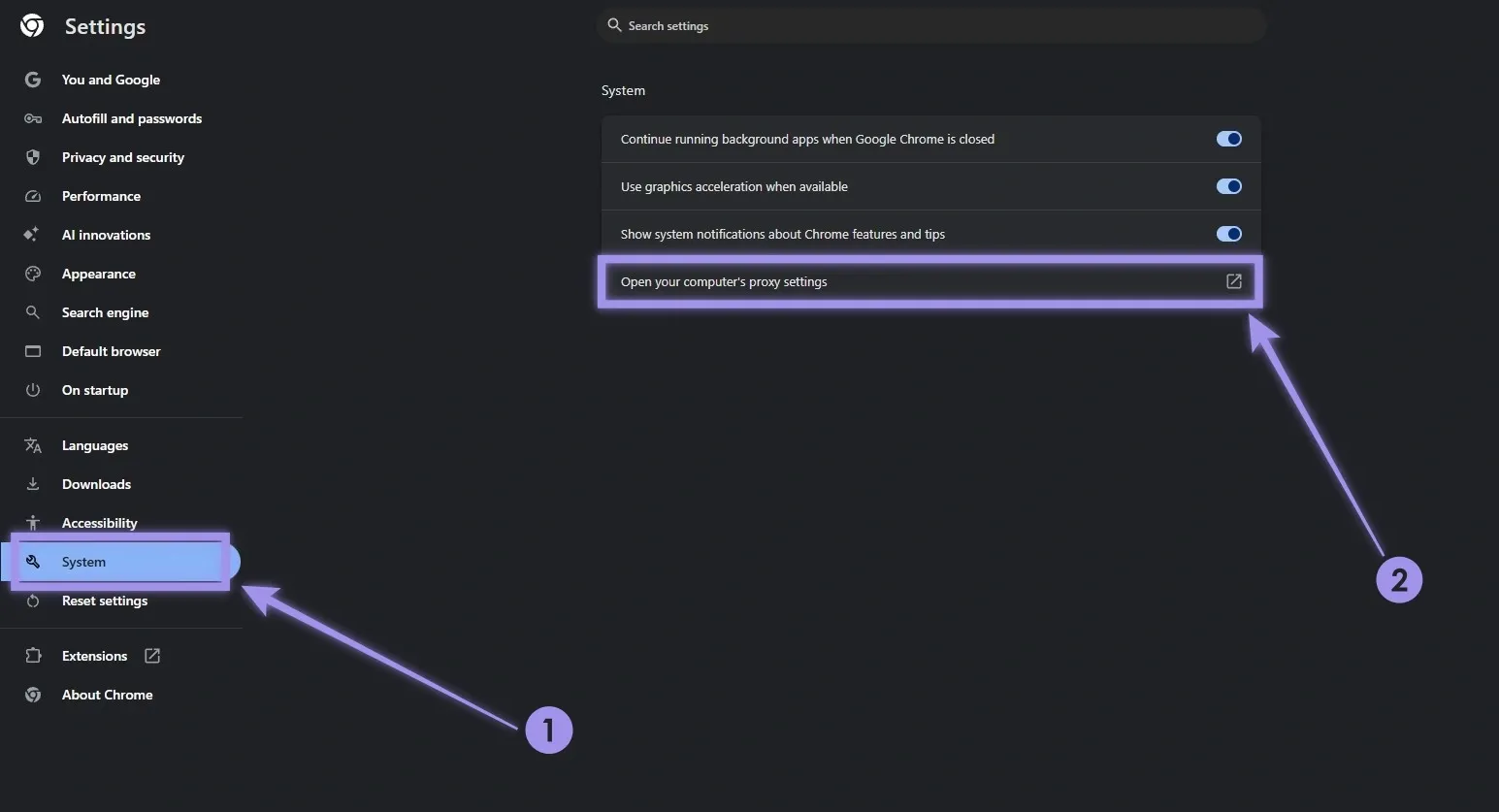
Google Chrome: Go to Settings > System > Open your computer’s proxy settings. This will open your OS proxy settings, and you can start setting up your proxies.
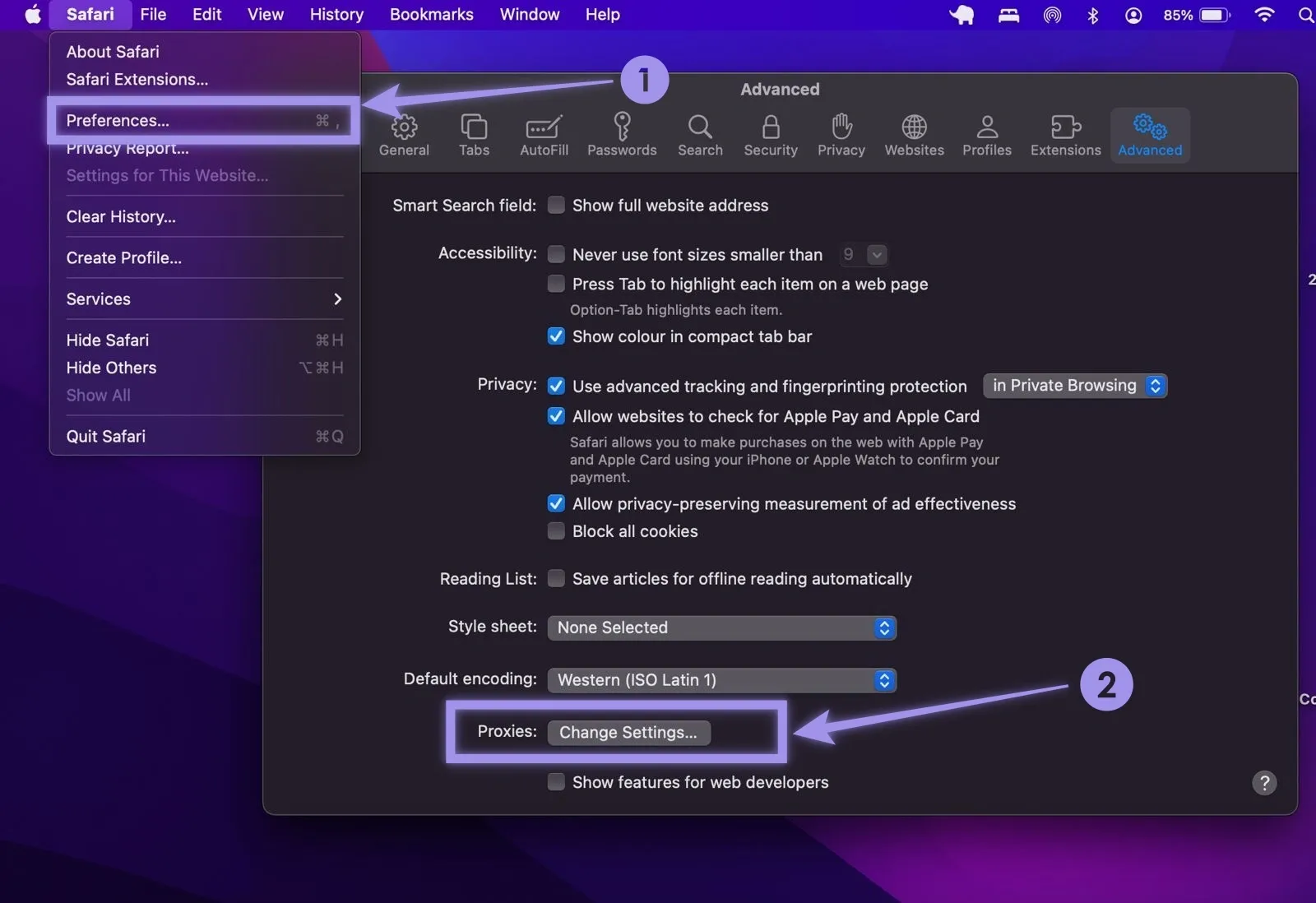
Safari: Open Safari > Preferences > Advanced > Proxies > Change Settings. Doing so opens macOS proxy settings, from which you can set up your proxy.
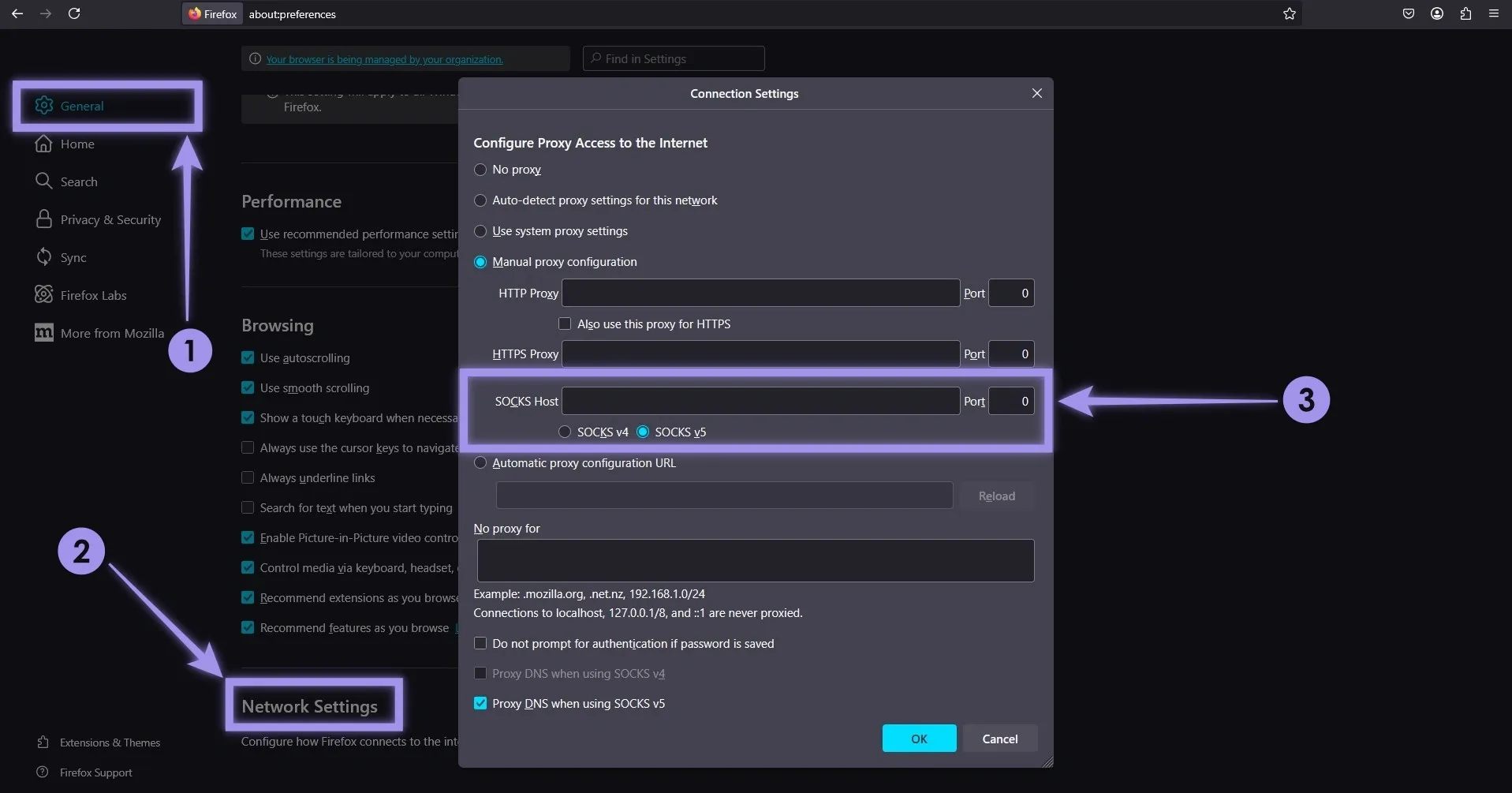
Firefox: Navigate to Settings > General > Network Settings. In the connection settings, you have a manual configuration for proxies—fill in your proxy details and set it up.
Setup Proxy on PC (Windows and macOS)
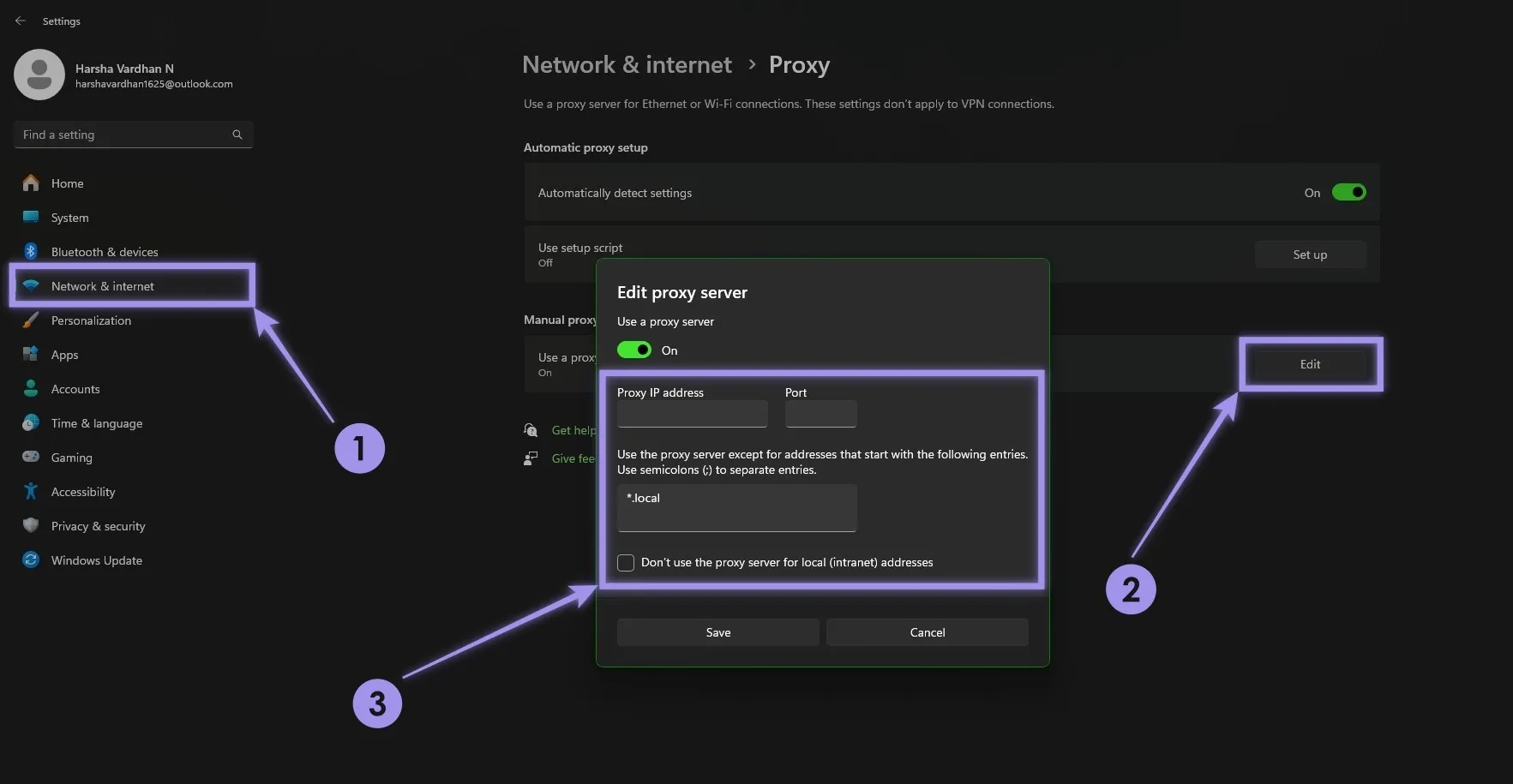
Windows: Go to Settings > Network & Internet > Proxy. Next, navigate to Manual proxy setup > Edit > Edit proxy server. Fill in the details and set up your proxy.
macOS: Go to System Preferences > Network > Advanced > Proxies. Now, choose the proxy and configure them to finish the setup.
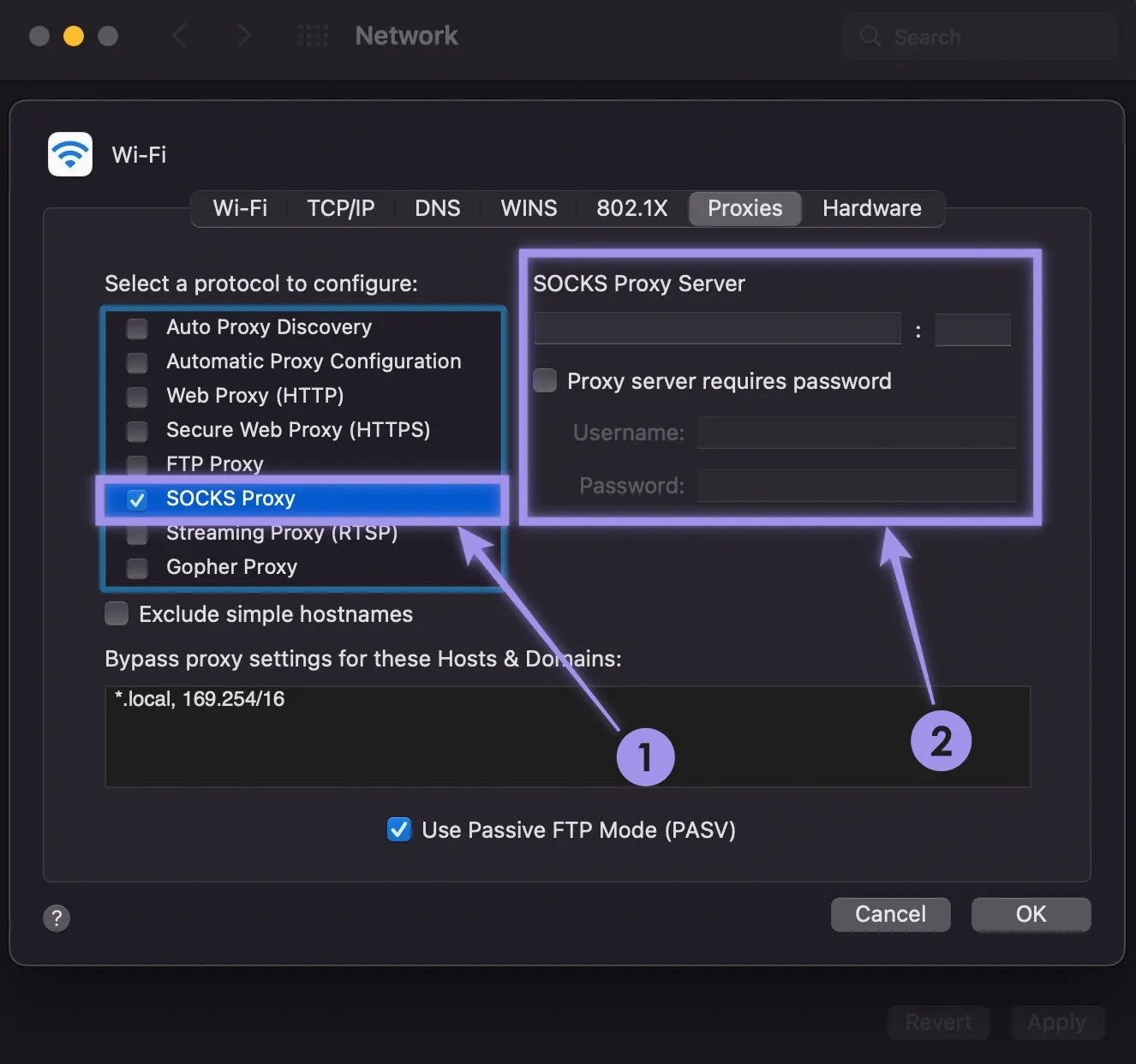
Note: Unfortunately, SOCKS proxies aren’t natively compatible with mobile devices (iOS and Android). However, you can still use apps that let you use your SOCKS5 proxies. While this approach offers a way around it, choose the right app to avoid inconsistencies with performance and stability.
SOCKS Proxy Use Cases and Applications
If you want to put SOCKS to the right use, learning its use cases and applications can be handy. While it has various use cases and applications, here are a few key ones.
- Web Scraping and Automation: Use SOCKS proxies to scrape websites without getting blocked. This is done through IP rotation and is often used with bots and automation to achieve stable and anonymous connections.
- Secure Access via SSH Tunnels: Developers or admins prefer SSH SOCKS proxies to access internal systems remotely. This is because the traffic can be encrypted, making it safe for temporary connections.
- Bypassing Geo-Restrictions: VPNs are often preferred to circumvent geo-restrictions. However, they become slow with the added encryption and can also become expensive. You can use SOCKS proxies instead to unlock region-locked content by choosing the desired region.
The biggest concern for many is to pick between proxies and VPNs. Couldn’t make a choice? Check out our VPN vs. Proxy comparison.
- Gaming and Reduced Ping: Gamers use SOCKS proxies to connect to servers in other regions or avoid IP bans. Choosing a nearby proxy can also reduce lag and improve stability.
- Accessing Blocked Websites: SOCKS proxies can bypass firewalls or network restrictions in schools, offices, or restricted countries. As they work at the application level, you get added flexibility with file types and different apps.
- Torrenting and P2P File Sharing: SOCKS5 (specifically) proxies work with popular torrent clients and support both TCP and UDP traffic. They help mask the user’s IP while keeping speeds fast.
- Ad Verification: Businesses and individual often rely on SOCKS proxies to check if their ads appear correctly in different locations. They benefit from it as they use it to detect fraud or unauthorized placements.
- Multi-Account Management: For social media or eCommerce, SOCKS proxies are often paired with browsers like SessionBox. This way, you can manage multiple accounts without getting flagged, as each account can be assigned a different IP using a proxy for added safety.
Challenges and Considerations
It’s clear that the SOCKS proxy brings a lot to the table, but there are a few scenarios where it falls short. We suggest keeping these in mind when you’re working with SOCKS proxies.
- Not Ideal for Privacy Alone: While SOCKS proxies hide your IP, they don’t offer complete privacy. If your goal is full online anonymity, using SOCKS alone might not be enough.
- No Built-in Encryption: SOCKS proxies don’t encrypt traffic by default. This means your data could be visible to your ISP or anyone snooping on unsecured networks—especially with public Wi-Fi.
- Manual Setup for Platforms and Apps: Not all platforms and applications support proxy settings out of the box. This scenario can make it difficult for non-technical users. You may need to rely on third-party tools or system-level configurations to make SOCKS work.
- Limited Traffic Filtering: SOCKS proxies don’t filter or block content. Pairing them with other tools is a must if you want to control traffic (like blocking ads or malware).
- Performance Depends on Provider: The speed and reliability of a SOCKS proxy heavily depend on where and how it's hosted. Low-quality or free proxies often lead to slow or unstable connections.
Conclusion
SOCKS proxies have steadily kept up with the needs of both individuals and businesses. They’re a reliable solution that can be applied across many different scenarios, from scraping and gaming to secure remote access.
That said, the real value comes down to how you use them. If your app or tool supports HTTP proxies, that’s often the best place to start. But if you need UDP support, native encryption via SSH, or you're working with apps that can’t use HTTP — SOCKS5, or SSH SOCKS proxies are strong alternatives.
In such a scenario, choose SOCKS proxies from a trusted provider (Ping Proxies offers ethically sourced proxies with low latency and high uptime). Then, make sure they're set up correctly—any small mistake can hold back their full potential.
